This blog post covers several topics that I should have made independent posts about… but anyway. Here we are. It’s September and I should have done this months ago.
Trezor / USB Hacking Updates (Black Hat + WOOT)
I had an earlier blog post with details of the Trezor attack. It turns out this is more generic type of attack than I realized, so I extended this work into a WOOT paper as well. Quickly I thought I should update on that…
To begin with – you can check out my Black Hat USA slides on the web at http://i.blackhat.com/USA-19/Wednesday/us-19-OFlynn-MINimum-Failure-Stealing-Bitcoins-With-EMFI.pdf .
Probably you want more details though, so luckily I included them in a paper presented at WOOT ’19 (see https://www.usenix.org/system/files/woot19-paper_oflynn_0.pdf).
This paper includes some additional details. One major thing is that the USB attack I used in the Trezor applies to many other devices. Basically almost everything has something like the following chunk of code:
if (∗length > setup−>wLength) {
∗length = setup−>wLength;
}The problem comes about because the wLength field ends up coming from the computer (host). Using fault injection we can always cause that code-path to be taken, meaning we can read out data directly from the target device. This applies in only certain circumstances… here is a quick flow-chart of when you should care:
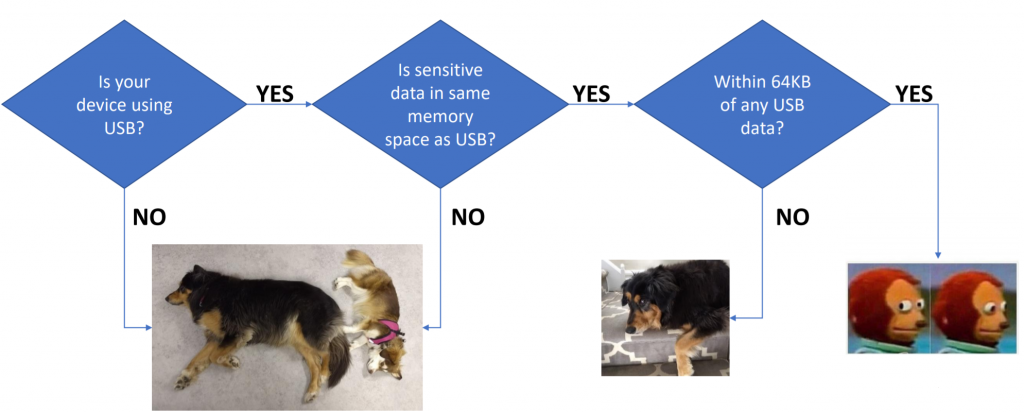
PhyWhisperer-USB
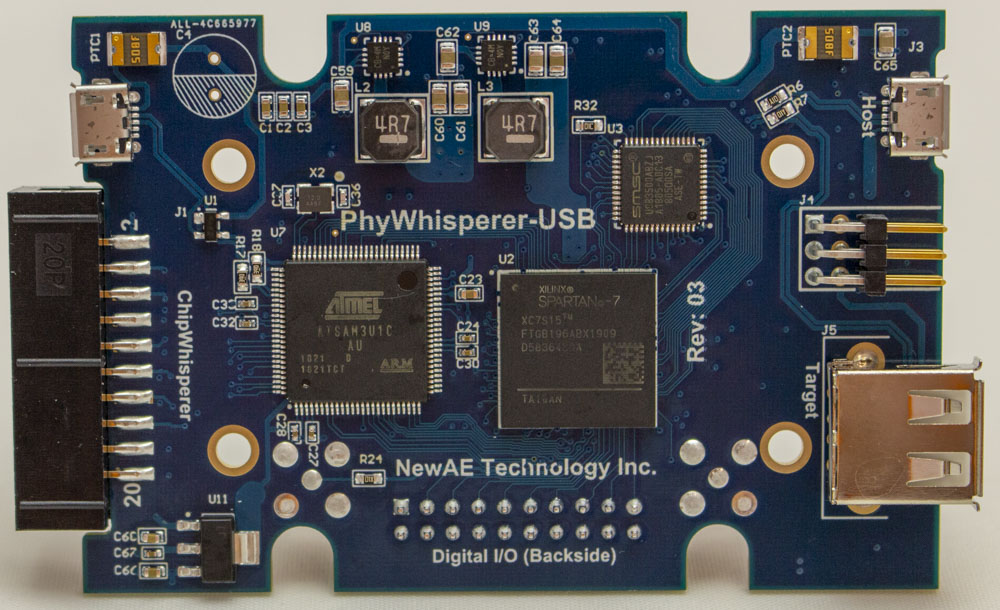
As part of this project, I also started a new open-source USB trigger logic device. You can check it out on
https://github.com/newaetech/phywhispererusb
We’re also doing a CrowdSupply for the initial run – see
https://crowdsupply.com/newae/phywhisperer-usb
Would it by possible to use the seek thermal module to send a thermal image via wireless connection to your computer?