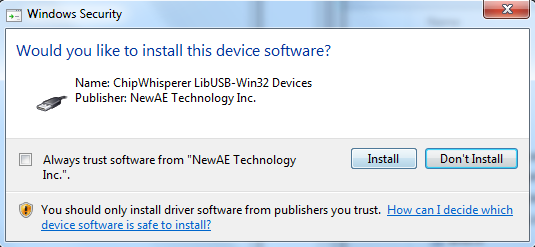
I recently wanted to sign some drivers to avoid requiring users of my ChipWhisperer device to do the usual bypass-signature deal. The end result is a sweet sweet screen like this when install the drivers:
If you are in this situation, I wanted to add some of my own notes into the mix.
David Grayson has an awesome guide which I mostly followed, available at http://www.davidegrayson.com/signing.
The steps I followed (again from his guide basically) are:
- Buy a Code Signing Certificate, I selected one from GlobalSign. They will verify your company information as part of this (or name if person) which basically involves calling you.
- Download the certificate. You can then double-click on it to install it into your system (hint: you may want to dedicate a VM or machine to this to keep your certificate off your laptop you travel with for example).
- You need the ‘signtool’ and ‘inf2cat’ programs. This requires install Windows SDK + Windows WDK (which itself depends on Visual Studio 2013). There’s like 10GB of other crap you install in order to get these files. Anyway install them…
- Write the following in a batch file:
"C:\Program Files (x86)\Windows Kits\8.1\bin\x86\inf2cat" /v /driver:%~dp0 /os:XP_X86,Vista_X86,Vista_X64,7_X86,7_X64,8_X86,8_X64,6_3_X86,6_3_X64 "C:\Program Files (x86)\Windows Kits\8.1\bin\x86\signtool" sign /v /n "Your Company Name Inc." /tr http://timestamp.globalsign.com/scripts/timestamp.dll *.cat "C:\Program Files (x86)\Windows Kits\8.1\bin\x86\signtool" sign /v /n "Your Company Name Inc." /tr http://timestamp.globalsign.com/scripts/timestamp.dll /fd SHA256 /as *.cat pause
- Copy the batch file to the directory with the .inf file, and double-click it.
- You might need to modify your .INF file, check the output for errors – I had to update the date to be past 2013 for example. The above will work if you’ve installed the certificate on your system, as it will search for a certificate with “Your Company Name Inc.”, so you need to match that exactly.
- Party – you should now have a signed .cat file! Distribute the whole batch (be sure to remove the .bat file) to your customers/users.
The batch file I use above signs both a SHA1 and SHA256 signature. SHA1 is being deprecated due to collision attacks (interesting sidenote: these were used as part of the attack on Iranian centrifuges by creating digitally signed drivers).
Unfortunately SHA256 isn’t fully supported across all platforms you might need to support (see https://support.globalsign.com/customer/portal/articles/1499561-sha-256-compatibility), so for now I’m using both, which I think works?