On April 1st, 2022 I gave a “workshop” at New England Hardware Security Day. This blog post is a quick summary of some of the links to recreate my demos from that talk. Here is a copy of the slides if you’d like them:
DFA on Raspberry Pi with PicoEMP

This demo is pretty simple – it recreates the classic DFA attack on RSA (I find David’s description great here, or you can see my Hardware Hacking Handbook which includes another derivation of it using a different method).
You can see the full code source in my repo from Hackaday Remoticon 2021. That repo just includes the R-Pi Python side (it also makes reference to voltage glitching, which I showed in the talk as another way to perform the demo).
You’ll need to install a specific version of pycryptodome along with a library that performs the analysis afterwards:
pip install pycryptodome==3.1
sudo apt-get install python3-gmpy2From there you can run rsaglitch.py – if you run it as-is it will sit there waiting for a fault. If you don’t have a FI generator or just want to see it work, simply uncomment the lines that include some example fault output.
The actual fault injection in my demo was done with the PicoEMP. This is a low-cost/open-source EMFI tool. Critically it doesn’t require dangerous exposure to high voltage that some other open-source tools inherently present.
Watch out with this demo – it can be annoying as you crash the R-Pi a lot while dialing it in! And it can take a while to boot, but I gaurantee you it will work!
RISC-V Soft-Core
This demo was based on one of the targets that will come with the ChipWhisperer-Husky, an iCE40 based FPGA target.
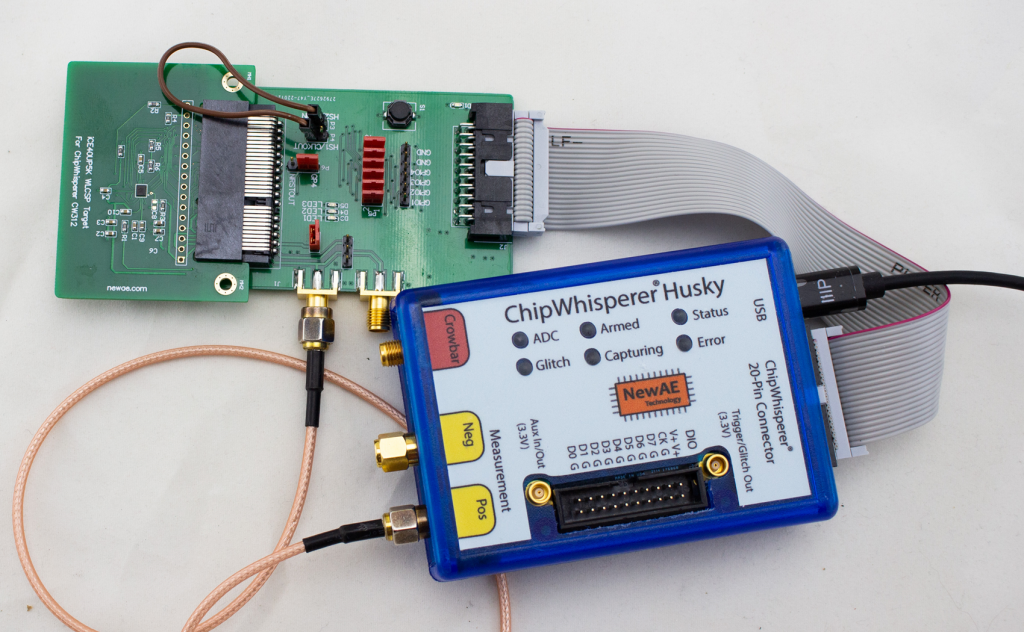
The soft-core in question is the excellent NEORV32 RISC-V core. I find that core’s got great documentation. You don’t need to build the core to use the existing design, as the ChipWhisperer repo has a pre-built binary of the FPGA image. So you can compile software for that image. But it’s fun to build your own core!
- Checkout the neorv32-setups repository.
- Follow instructions to configure the required FPGA toolchain (the ‘osflow’ toolchain).
- Run
make BOARD=iCE40CW312 MinimalBoot
Hardware ECC Attacks
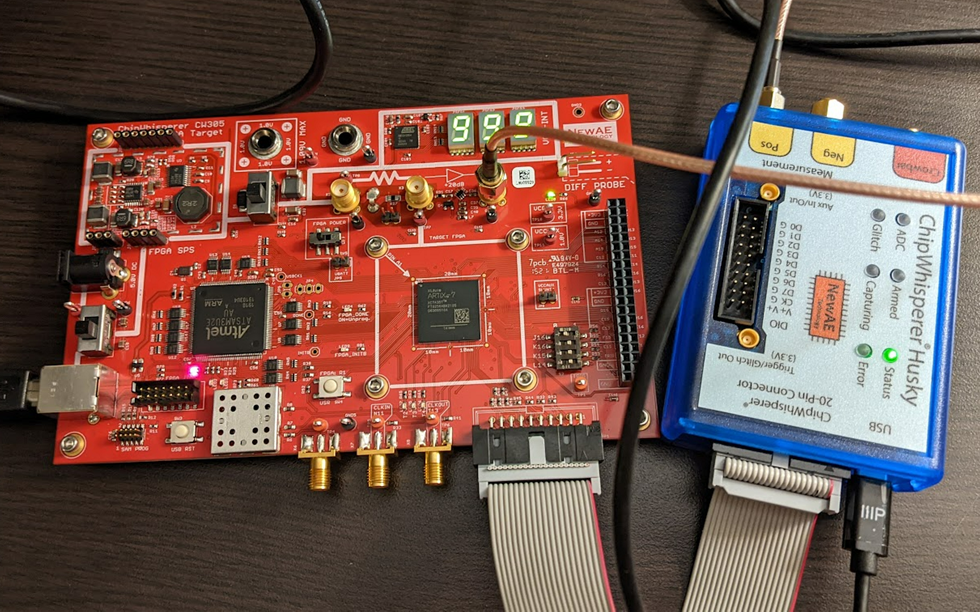
This demo uses the ChipWhisperer CW305 board (here in the A35 variant), which has a series of nice ECC jupyter notebook tutorials . These tutorials will walk you through how the entire attack works:
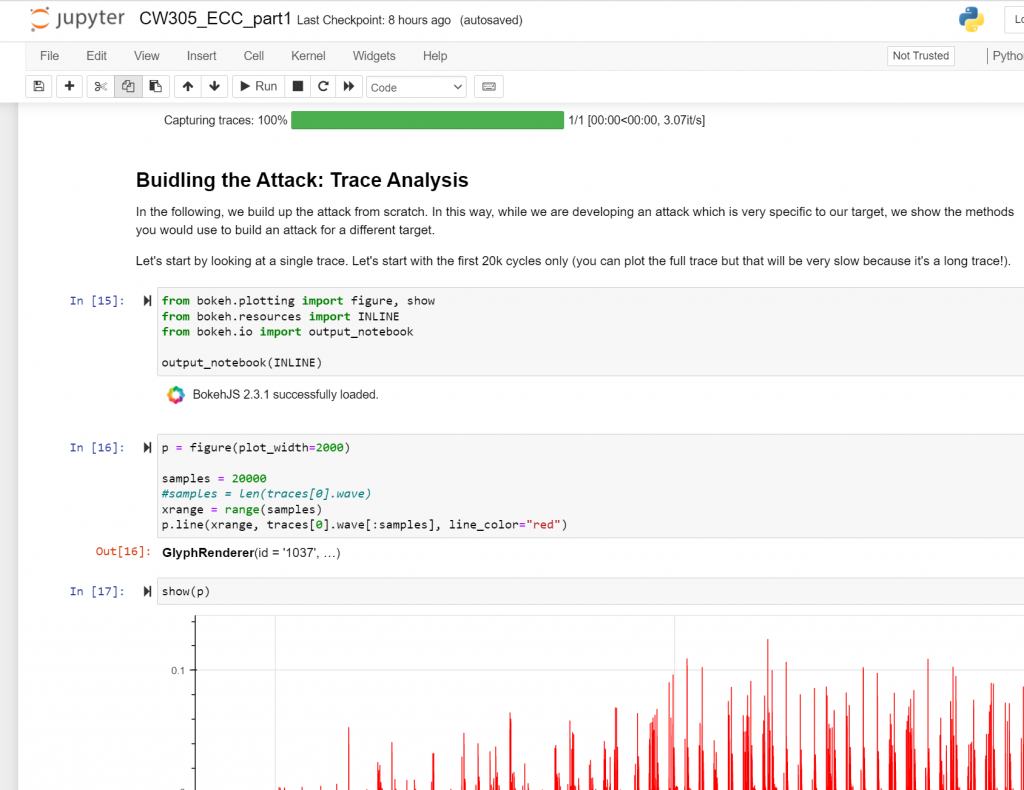
The ECC core is based on the excellent and open-source CrypTech project.
We have a detailed write-up of the attack that can also be helpful to see!